![]()
Bypass 802.1x Port Security w/ Openwrt
Background
During an internal and wireless penetration I was unprepared for the port security in the environment. I had to travel internationally and the Statement of Work and Rules of Engagement did not detail the extent of the internal testing and what was to be tested. Penetration Testers know what it is like to conduct a “Penetration Test” when sales staff and client management setup the engagement. Needless to say I was upset at the delay only due to the time it would take to configure a device to bypass the port security when I only had a week onsite to conduct the testing. Luckily I had brought along my PCEngines Alix 62f (used previously in my Custom Power Pwn). I had brought it for the wireless testing as it was configured for wireless client attacks. Using the work done by Alva Lease ‘Skip’ Duckwall IV and presented at DEFCON 19 in 2011. I reconfigured the Alix to show the client how easy it is to bypass port security. Well I never want to encounter a similar situation again but I also don’t want to carry yet another device with me when traveling. Having the device be as small as possible while service multiple purposes would be ideal. That is why I’m using the GL-iNet with the Openwrt operating system for this project.
Version 2 of this tutorial builds off of version 1 but additional work is done to help you build an image that will allow you to bypass 802.1x port security without any post install customization (as shown in this previous post). Also some network recon tools are included as well.
Obtaining Openwrt
*Note: Everything is done from the latest version of Ubuntu LTS (14.04).
For this tutorial we will work out of your home directory. We will download the latest code for Openwrt Attitude Adjustment 12.09 (AA) and a patch from the GL-iNet website. We will also need to modify two files so that we can compile the 16mb image of AA for the GL-iNet. The two files we will modify are ar71xx/image/Makefile and firmware-utils/src/mktplinkfw.c.
But first we will apply the AA patch provided by GL-iNet using the utility quilt.
Make sure your environment has the software required, including quilt.
$ sudo apt-get update
$ sudo apt-get install git-core build-essential libssl-dev subversion libncurses5-dev zlib1g-dev gawk gcc-multilib flex gettext quilt xsltproc libxml-parser-perl mercurial bzr ecj cvs unzip
To setup quilt you want a file called .quiltrc in your home directory with the following lines:
QUILT_DIFF_ARGS="--no-timestamps --no-index -pab --color=auto"
QUILT_REFRESH_ARGS="--no-timestamps --no-index -pab"
QUILT_PATCH_OPTS="--unified"
QUILT_DIFF_OPTS="-p"
EDITOR="nano"
How you accomplish this is up to you. Open gedit and paste, open vim and paste, or do the following from the command line.
$ echo -e QUILT_DIFF_ARGS="--no-timestamps --no-index -pab --color=auto"'\n'QUILT_REFRESH_ARGS="--no-timestamps --no-index -pab"'\n'QUILT_PATCH_OPTS="--unified"'\n'QUILT_DIFF_OPTS="-p"'\n'EDITOR="nano" > ~/.quiltrc
Move to your home directory obtain AA, update and download the package source files, and patch it using quilt.
$ cd ~/
$ git clone git://git.openwrt.org/12.09/openwrt.git attitude_adjustment
$ cd attitude_adjustment
~/attitude_adjustment$ git clone https://github.com/alzhao/Openwrt-patches-for-GL.iNet.git patches
~/attitude_adjustment$ echo 000-gl_aa1209.patch > patches/series
~/attitude_adjustment$ quilt push -a
Download and install all available “feeds”, create our configuration file to build what we need.
$ cd ~/attitude_adjustment
~/attitude_adjustment$ ./scripts/feeds update -a
~/attitude_adjustment$ ./scripts/feeds install -a
~/attitude_adjustment$ make menuconfig
Go forth and select all of these packages to be included in the image and not as a modules (asterisk (*) instead of (M)).
Network —> (mii-tool & tcpdump)
Network —>Firewall (arptables & ebtables)
Network —>Firewall—>iptables (iptables-mod-conntrack-extra, iptables-mod-extra, iptables-mod-filter, iptables-mod-iface, iptables-mod-ipopt, iptables-mod-ipset, iptables-mod-ipv4options, iptables-mod-nat-extra, iptables-mod-rawnat, iptables-mod-tee)
Kernel modules —>Netfilter Extensions (kmod-arptables, kmod-ebtables, kmod-ebtables-ipv4, kmod-ebtables-ipv6)
Kernel modules —>Network Support (kmod-bridge, kmod-llc, kmod-stp)
Libraries —>(libpcap,wireless-tools)
Base system —>busybox Networking Utilities —>arp
Kernel modules —>Filesystems (kmod-fs-ext4, kmod-fs-ntfs & kmod-fs-vfat)
Kernel modules —>USB Support (kmod-usb-ohci, kmod-usb-uhci, kmod-usb2, kmod-usb-storage, kmod-usb-storage-extras)
Kernel modules —>Native Language Support (kmod-nls-cp437, kmod-nls-base & kmod-nls-iso8859-1)
“Hacker” Tools
Network —>NMAP Suite (ncat-ssl,ndiff,nmap-ssl,nping)
Network —>wireless (aircrack-ng,aircrack-ptw,kismet-client,kismet-server,reaver)
Libraries —>(libcap,libncurses,libnl,libpcre,terminfo,uclibcxx,zlib)
Libraries —>SSL (libopenssl)
Base system —>(libstdcpp)
Custom Files
The best place to learn about adding custom files to your image build is the OpenWrt Wiki, specifically here.
Create Directories to Store Out Custom Files
$ mkdir -p ~/attitude_adjustment/files/etc/init.d
$ mkdir -p ~/attitude_adjustment/files/etc/config
$ mkdir -p ~/attitude_adjustment/files/etc/rc.d
Custom Wireless Configuration Files
$ vim ~/attitude_adjustment/files/etc/config/wireless
config wifi-device radio0
option type mac80211
option channel 11
option hwmode 11ng
option path 'platform/ar933x_wmac'
option htmode HT20
list ht_capab SHORT-GI-20
list ht_capab SHORT-GI-40
list ht_capab RX-STBC1
list ht_capab DSSS_CCK-40
config wifi-iface
option device radio0
option network lan
option mode ap
option ssid att-wifi #or whatever you want to call it
option encryption psk2
option key 'mysupersecretPassWord'
option hidden 1
Custom Network Configuration Files
$ vim ~/attitude_adjustment/files/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
Custom System Configuration Files
$ vim ~/attitude_adjustment/files/etc/config/system
config system
option hostname GLiNet #or whatever you want to call it
option timezone UTC
Custom System Control Configuration File
$ vim ~/attitude_adjustment/files/etc/sysctl.conf
kernel.panic=3
net.ipv4.conf.default.arp_ignore=1
net.ipv4.conf.all.arp_ignore=1
net.ipv4.ip_forward=1
net.ipv4.icmp_echo_ignore_broadcasts=1
net.ipv4.icmp_ignore_bogus_error_responses=1
net.ipv4.tcp_ecn=0
net.ipv4.tcp_fin_timeout=30
net.ipv4.tcp_keepalive_time=120
net.ipv4.tcp_syncookies=1
net.ipv4.tcp_timestamps=1
net.ipv4.tcp_sack=1
net.ipv4.tcp_dsack=1
net.ipv6.conf.default.forwarding=1
net.ipv6.conf.all.forwarding=1
net.netfilter.nf_conntrack_acct=1
net.netfilter.nf_conntrack_checksum=0
net.netfilter.nf_conntrack_max=16384
net.netfilter.nf_conntrack_tcp_timeout_established=3600
net.netfilter.nf_conntrack_udp_timeout=60
net.netfilter.nf_conntrack_udp_timeout_stream=180
There are four files in the tarball and it is just easier to provide the files then figure out how to disable some of this shit in OpenWrt. Included in the tarball is the bridge script you will need to create the transparent bridge. But also included are dnsmasq, firewall, and telnet files with permissions where execution is removed. Best way to disable them without removing them.
$ cd ~/attitude_adjustment/files/etc/
~/attitude_adjustment/files/etc$ wget http://www.jedge.com/code/glinet.openwrt.init.d.build.tar.gz
tar xzvf glinet.openwrt.init.d.build.tar.gz
Create a symlink for the bridge script so it will start when the device boots.
$ cd ~/attitude_adjustment/files/etc/rc.d
~/attitude_adjustment/files/etc/rc.d$ ln -s ../init.d/bridge S90bridge
~/attitude_adjustment/files/etc/rc.d$ ln -s ../init.d/bridge K95bridge
Why set your root password after the first boot? Why not set it in your image before you install it?
echo "yoursecret" | makepasswd --clearfrom=- --crypt-md5 |awk '{print $2}'
$1$uZ9fJ7OE$A8KGOGcOR4fP3/XEsxQaa0
$ vim ~/attitude_adjustment/files/etc/shadow
root:$1$uZ9fJ7OE$A8KGOGcOR4fP3/XEsxQaa0:0:0:99999:7:::
daemon:*:0:0:99999:7:::
ftp:*:0:0:99999:7:::
network:*:0:0:99999:7:::
nobody:*:0:0:99999:7:::
Move back to the home directory and obtain the latest trunk of Openwrt. We do this because we want to copy two files from Openwrt trunk to AA that include information for building a 16mb firmware for the GL-iNet. Then we remove the trunk downloaded.
$ cd ~/
$ git clone git://git.openwrt.org/openwrt.git openwrt_trunk
$ cp ~/openwrt_trunk/tools/firmware-utils/src/mktplinkfw.c ~/attitude_adjustment/tools/firmware-utils/src/mktplinkfw.c
$ cp ~/openwrt_trunk/target/linux/ar71xx/image/Makefile ~/attitude_adjustment/target/linux/ar71xx/image/Makefile
$ rm -rf openwrt_trunk
Now we can compile our image. Once complete your image will be find in
~/attitude_adjustment/bin/ar71xx called
openwrt-ar71xx-generic-gl-inet-6416A-v1-squashfs-factory.bincd ~/attitude_adjustment
~/attitude_adjustment$ make
Documenting how to upgrade (or downgrade) the firmware of your GL-iNet is tricky as I don’t know the state of your device so we are going to use a method I’m sure you haven’t messed with. We are going to use the U-boot Web Method of upgrading. You will need to pry open your GL-iNet and connect a serial to USB adapter as documented from the GL-iNet website. Visit the two links below.
http://www.gl-inet.com/docs/smartrouter/?diy_hardware.html
http://www.gl-inet.com/docs/smartrouter/?diy_serial.html
Then boot your device and enter the web failsafe mode following the directions also found on the GL-iNet website.
http://www.gl-inet.com/docs/smartrouter/?diy_flashing.html
Connect to your USB serial device and then plug in your GL-iNet. Immediately hit the “F” key to enter the U-boot mode and enter httpd to start the failsafe web server. We will need to connect to the WAN port and assign an IP address in the 192.168.1.0/24 range, open a web browser, and go to http://192.168.1.1
From the web interface upload the firmware you compiled. It should be called openwrt-ar71xx-generic-gl-inet-6416A-v1-squashfs-factory.bin.
References
A Bridge Too Far Defeating Wired 802.1X with a Transparent Bridge Using Linux by Alva Lease ‘Skip’ Duckwall IV
Presentation Slides: https://www.defcon.org/images/defcon-19/dc-19-presentations/Duckwall/DEFCON-19-Duckwall-Bridge-Too-Far.pdf
Presentation (Youtube): http://youtu.be/u3T3lUxKm18
Issue discussing the use of ebtables and packets not being forwarded up the IP chain. The reason we had to re-enable bridged firewalling in Openwrt. http://stackoverflow.com/questions/17116126/iptables-ebtables-bridge-utils-prerouting-forward-to-another-server-via-single
Also mentioned in getting SSLStrip to work in a hak5.org forum. https://forums.hak5.org/index.php?/topic/26780-guide-for-installing-sslstrip-on-openwrt/
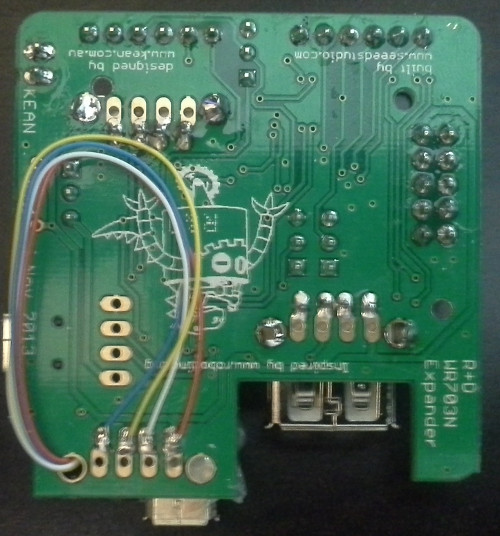
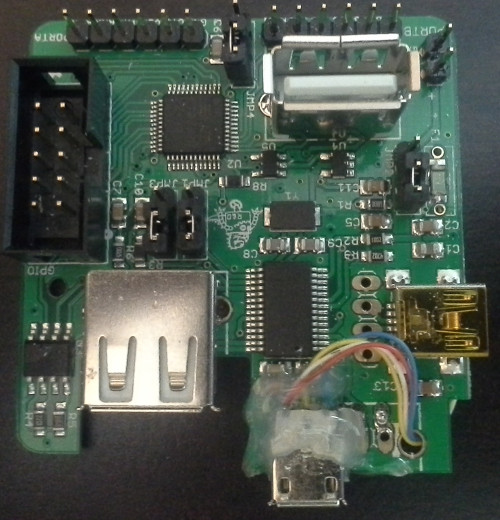



 In 2013 I presented at the
In 2013 I presented at the 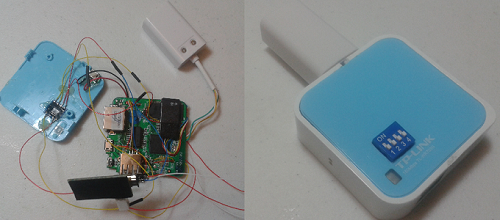


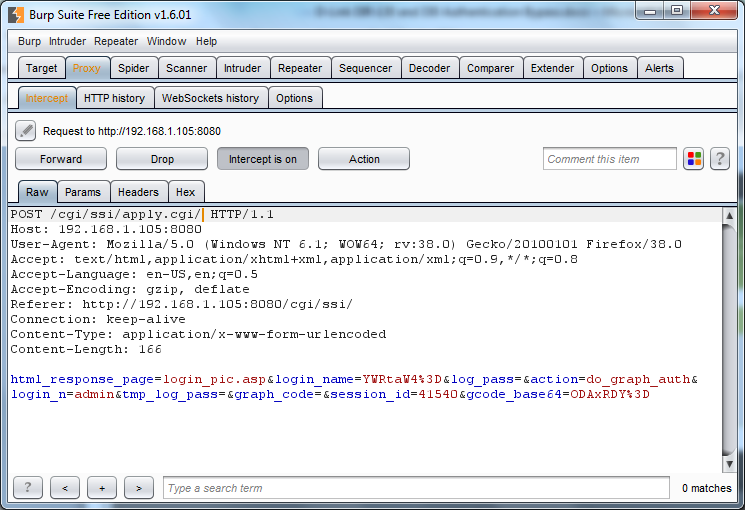
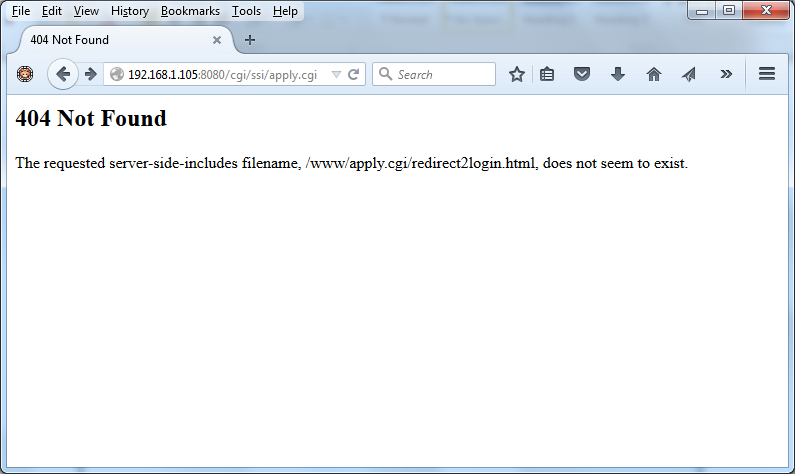
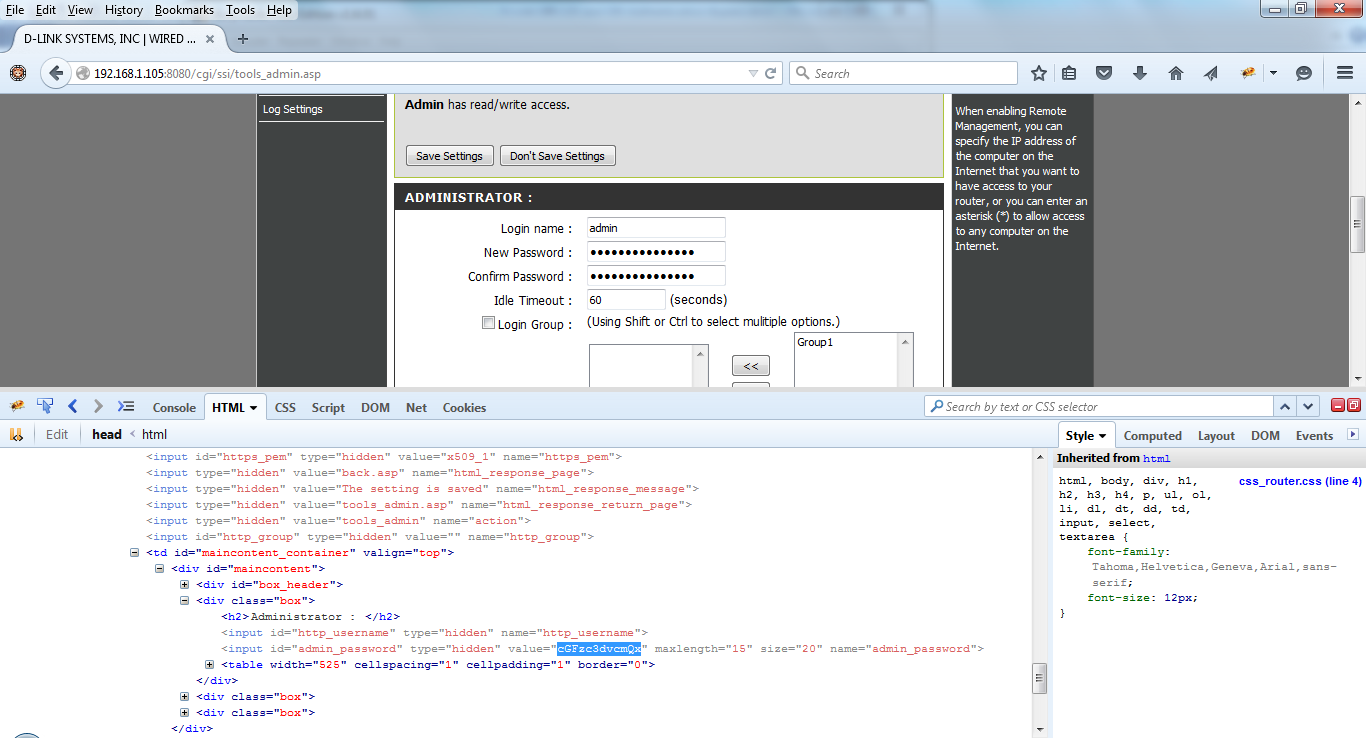
 A great place to pick up outdated, and potentially vulnerable, wireless routers is your local Goodwill. Depending on the store those shelves can be packed with devices for only a couple bucks. While you are there you can just Google the model number followed by “exploit” or “openwrt” to see if you have a device worth playing with. Today I got a Netgear WNR1000v2 and will detail my quick adventures with this device.
A great place to pick up outdated, and potentially vulnerable, wireless routers is your local Goodwill. Depending on the store those shelves can be packed with devices for only a couple bucks. While you are there you can just Google the model number followed by “exploit” or “openwrt” to see if you have a device worth playing with. Today I got a Netgear WNR1000v2 and will detail my quick adventures with this device.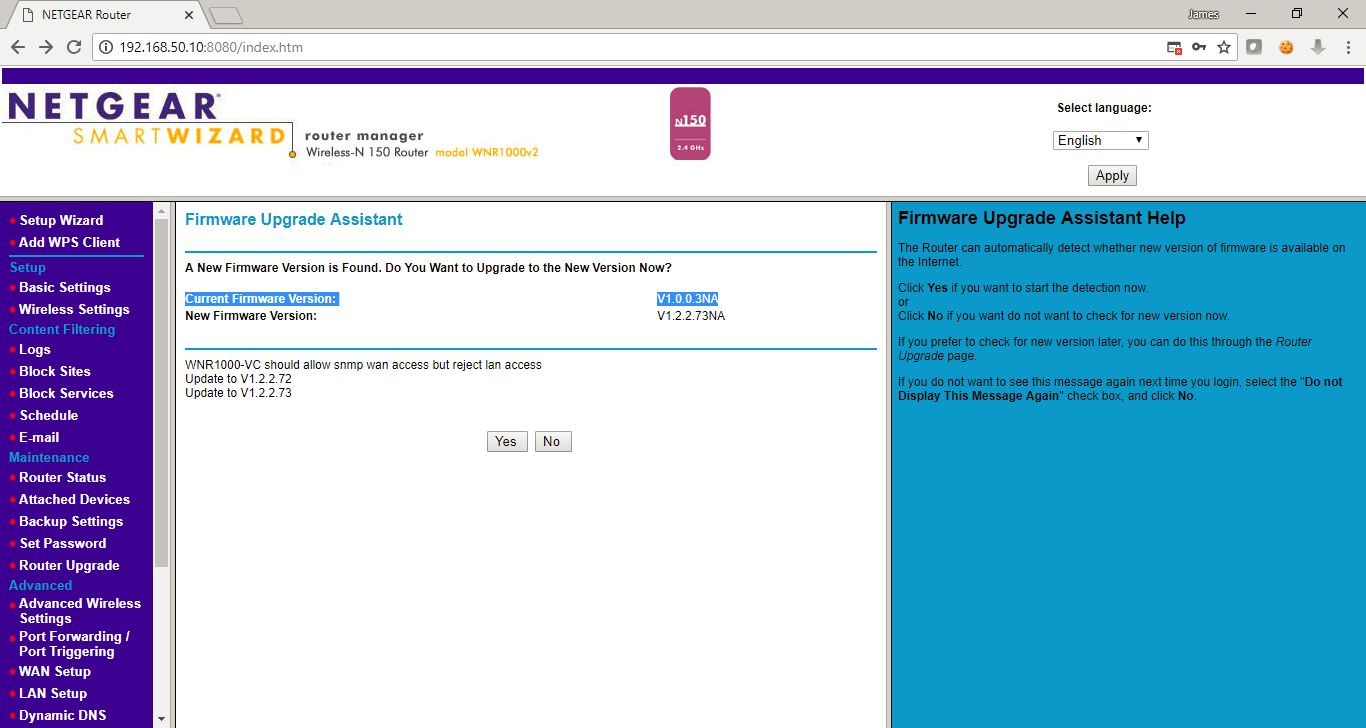









 As I’ve written about previously, a great place to pick up outdated, and potentially vulnerable, wireless routers is your local Goodwill. Depending on the store those shelves can be packed with devices for only a couple bucks. While you are there you can just Google the model number followed by “exploit”, “openwrt”, or “dd-wrt” to see if you have a device worth playing with. Today I got a Netgear WGT624v2 which dates back to POTUS 43’s first term. I will detail a different adventure than my
As I’ve written about previously, a great place to pick up outdated, and potentially vulnerable, wireless routers is your local Goodwill. Depending on the store those shelves can be packed with devices for only a couple bucks. While you are there you can just Google the model number followed by “exploit”, “openwrt”, or “dd-wrt” to see if you have a device worth playing with. Today I got a Netgear WGT624v2 which dates back to POTUS 43’s first term. I will detail a different adventure than my 
 This is a quick blog post on my thoughts regarding PCI-DSS password requirement 8.2.3 and how I think it creates an environment where all non-CDE data is left exposed via weak password requirements. I still see organizations that do not understand password strength vs password length and PCI-DSS 8.2.3 requires neither! I like to back up my posts with some data and statistics so feel free to use this information to let your auditors know that compliance does not equal secure. I show how quickly
This is a quick blog post on my thoughts regarding PCI-DSS password requirement 8.2.3 and how I think it creates an environment where all non-CDE data is left exposed via weak password requirements. I still see organizations that do not understand password strength vs password length and PCI-DSS 8.2.3 requires neither! I like to back up my posts with some data and statistics so feel free to use this information to let your auditors know that compliance does not equal secure. I show how quickly 








